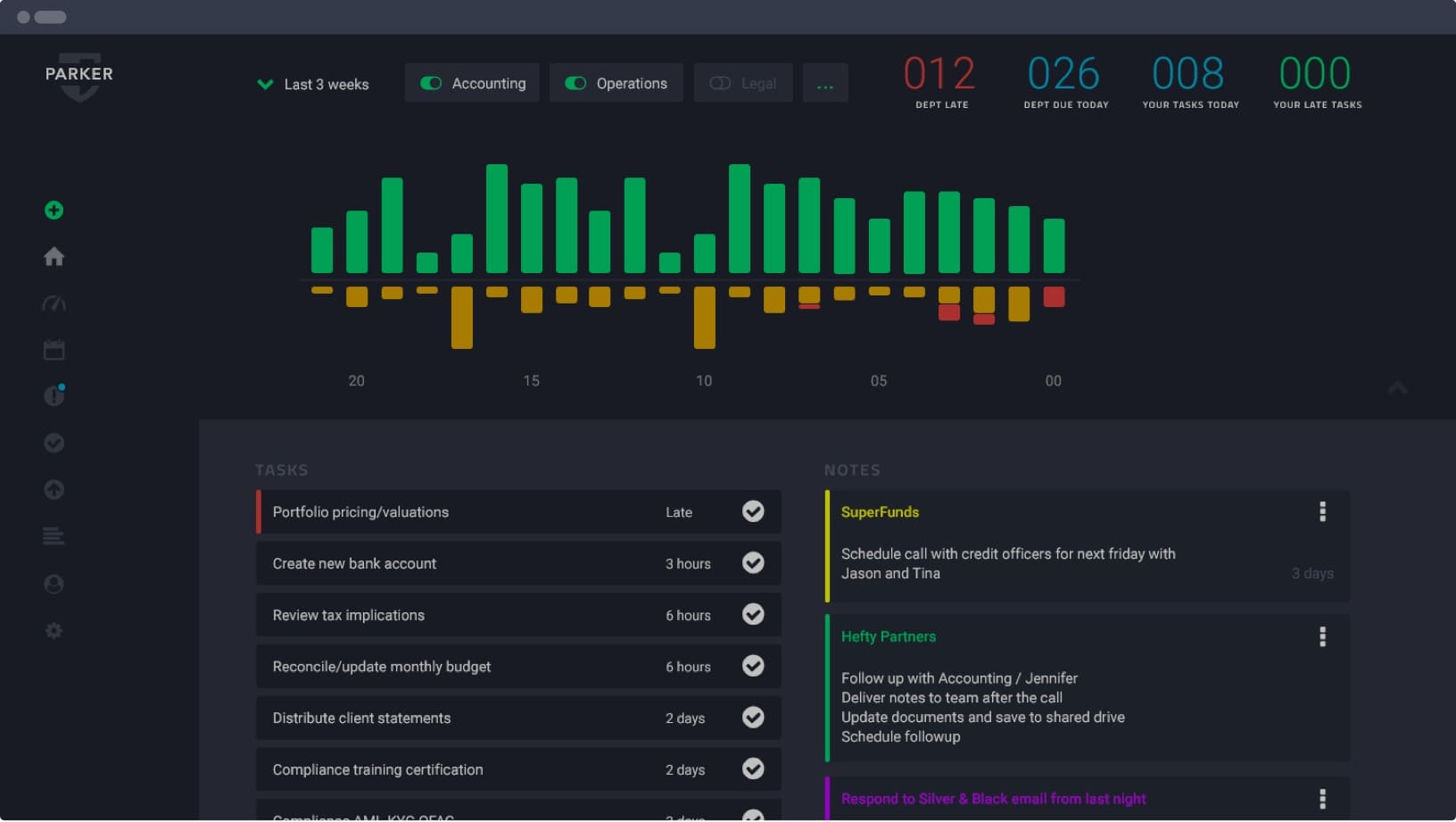
Asset Management Workflow
How can Asset Management Firms & RIA’s use OpsCheck?
customized to fit and adapt to any type of financial firm around the globe.
Future operational technology
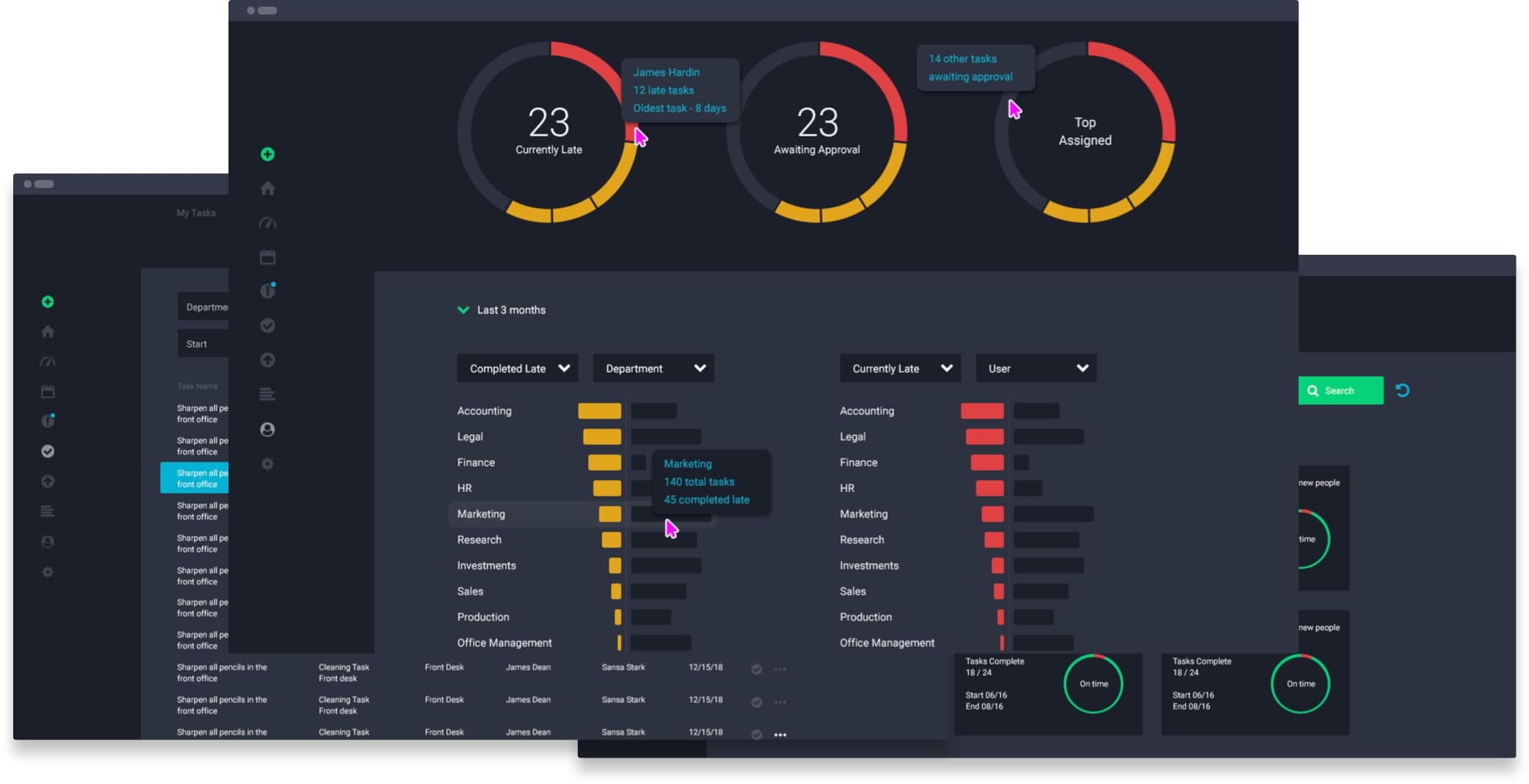
Deep operational visibility
Thorough operational control
How to Use Asset Management Workflow
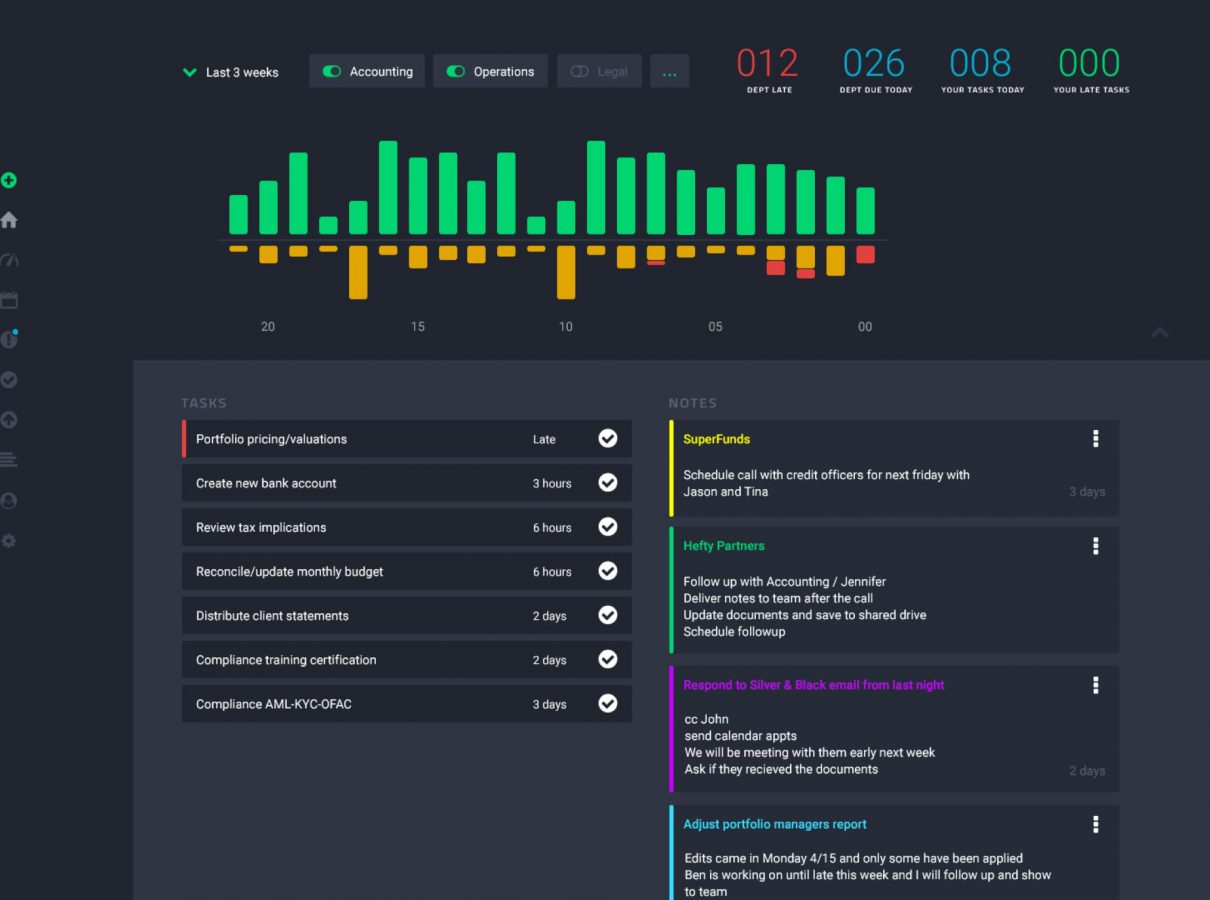
- Centralized task management workflow and oversight
- Powerful visual reporting and notifications
- Adaptation to any type of business of any size
- Easy collaboration, communication, and document storage
- Greatly improved team efficiency and accountability
- Coordination across teams, offices, and time zones
- Flexible integration with third-party applications
- Centralized communication hub for the entire firm
- Provide transparency to regulators and clients
Order for Asset Management Workflow

OpsCheck Testimonial: Jason Gunn
linkedintwitterOpsCheck has helped crypto-fintech company Quoine improve customer support, operations, and compliance. The solution has also made Head of Customer Support Jason Gunn’s job much easier. Gunn uses OpsCheck to assign and share tasks with the Japan-based...
Digital Transformation in the Financial Sector
Success and change in the financial industry have always been driven by three major forces: client demands, business competition, and innovation. With the advent of the internet, these pressures increased dramatically with clients and customers demanding fast quality services, regulators and auditors expanding asset managers’ obligations, and nimble start-up challengers like online banking and other financial service providers making inroads into the mobile markets.
OpsCheck Spotlights Covid Needs: Data Security (6/6)
With the move to remote working environments due to COVID 19, automated data systems as well as communications platforms have become critical tools for the continued functioning of asset management firms.
As part of the firm’s security measures, regular reviews and testing of technology systems should be incorporated. OpsCheck can support staff coordinate these efforts by tracking who or what is accessing software, files, and third-party vendors. Increased remote access to systems also leads to increased opportunity for unauthorized personnel and even malicious hackers to gain access to sensitive information or, worse, client accounts themselves.
Does OpsCheck have different levels of user access?
Is my firm’s activity in OpsCheck auditable?
Can I access OpsCheck from my mobile devices?
Does OpsCheck support two factor authorization and/or SAML login?
Does OpsCheck integrate with third party apps?
Will my data be safe?